What the Critical Erlang SSH Vulnerability Means for Elixir Developers
Michael Lubas, 2025-04-17

CVE-2025-32433, an Unauthenticated Remote Code Execution in Erlang/OTP SSH was announced yesterday. From the description:
A serious vulnerability has been identified in the Erlang/OTP SSH server that may allow an attacker to perform unauthenticated remote code execution (RCE). By exploiting a flaw in SSH protocol message handling, a malicious actor could gain unauthorized access to affected systems and execute arbitrary commands without valid credentials.
All users running the Erlang/OTP SSH server are impacted by this vulnerability, regardless of the underlying Erlang/OTP version. If your application provides SSH access using the Erlang/OTP SSH library, assume you are affected.
Affected versions Patched versions
<= OTP-27.3.2 OTP-27.3.3
<= OTP-26.2.5.10 OTP-26.2.5.11
<= OTP-25.3.2.19 OTP-25.3.2.20On the GitHub security page for Erlang/OTP, the severity is 10/10 critical, meaning if you are running an application that exposes Erlang’s SSH daemon to the public internet, anyone who knows how to exploit this vulnerability can hack into your server. An exploit has been published.
Are You Affected?
You have Elixir/Phoenix applications deployed to the open internet:
Most likely no. The default configuration for Phoenix does not expose the Erlang SSH daemon to the public internet. It is technically possible you are vulnerable if your application does expose Erlang’s SSH daemon, for example Elixir sftp clients do this.
Your Elixir/Phoenix application may be hosted on AWS, GCP, Gigalixir, Fly.io, or really any hosting provider. Most PaaS hosting providers (Gigalixir, Heroku, etc) do not allow you to open ports to the public internet, so if you are on a PaaS, you are safe. Fly.io does allow this via the external port ranges feature, released in 2023. With a cloud provider (AWS, GCP, Hetzner), you have the ability to expose the Erlang SSH daemon, so there is a small chance you are vulnerable, however this would require you to manually configure the daemon and expose it, which most people do not do. There are instructions below on how to check your exposure.
You are using Nerves for embedded/IoT devices:
If you are running SSH in production and have the port exposed to the public internet, yes. If you have SSH turned off in production, or you are tunneling SSH over a VPN so the device’s SSH daemon is not exposed to the internet, no. NervesSSH wraps Erlang/OTP’s SSH daemon. The Nerves team released an update to fix affected devices.
How to Check Your Exposure
If you go on Shodan and search “Erlang SSH” there are several public servers which return the string:
SSH-2.0-Erlang/4.9.1.3\r\n
These servers are vulnerable. When you are port scanning your environment, if you see a similar string returned by an internet facing server, check the version number. The patch for CVE-2025-32433 was applied in the following versions of Erlang’s SSH:
5.2.10 https://erlang.org/download/OTP-27.3.3.README.md
5.1.4.8 https://erlang.org/download/OTP-26.2.5.11.README
4.15.3.12 https://erlang.org/download/OTP-25.3.2.20.README
If the version returned is lower than these values, such as 4.9.1.3, then the server is vulnerable.
I recommend using nmap to check endpoints in your environment. Here is an example port scan of a server running Elixir/Phoenix:
nmap -p- -T5 --min-rate=10000 --max-retries=1 <target>
@ ~ % sudo nmap -p- -T5 --min-rate=10000 --max-retries=1 dev.paraxial.io
Starting Nmap 7.94 ( https://nmap.org ) at 2025-04-17 10:15 EDT
Nmap scan report for dev.paraxial.io (52.1.190.78)
Host is up (0.0011s latency).
rDNS record for 52.1.190.78: ec2-52-1-190-78.compute-1.amazonaws.com
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp closed domain
80/tcp open http
443/tcp open https
Nmap done: 1 IP address (1 host up) scanned in 13.50 secondsThis server is not vulnerable, because there are no ports accepting SSH connections.
@ ~ % sudo nmap -p- -T5 --min-rate=10000 --max-retries=1 app.blackcatprojects.xyz
Starting Nmap 7.94 ( https://nmap.org ) at 2025-04-17 09:45 EDT
Nmap scan report for app.blackcatprojects.xyz (95.217.236.73)
Host is up (0.12s latency).
Other addresses for app.blackcatprojects.xyz (not scanned): 37.27.194.25
rDNS record for 95.217.236.73: static.73.236.217.95.clients.your-server.de
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
Nmap done: 1 IP address (1 host up) scanned in 13.97 secondsThis server does accept SSH connections, so check the service on the SSH port:
@ ~ % nc app.blackcatprojects.xyz 22
SSH-2.0-OpenSSH_9.6p1 Ubuntu-3ubuntu13.8
This is running OpenSSH, which is not Erlang’s SSH daemon, so the server is not vulnerable. If the above string was SSH-2.0-Erlang, the server would be vulnerable.
Note that PaaS hosting providers (Gigalixir, Heroku, etc) do not allow you to open ports, so these port scans will not work because you do not even have the option to expose the Erlang SSH daemon to the public internet.
Paraxial.io Customers
If you are a Paraxial.io customer, the Network Scans feature automatically banner grabs the SSH version running on port 22:
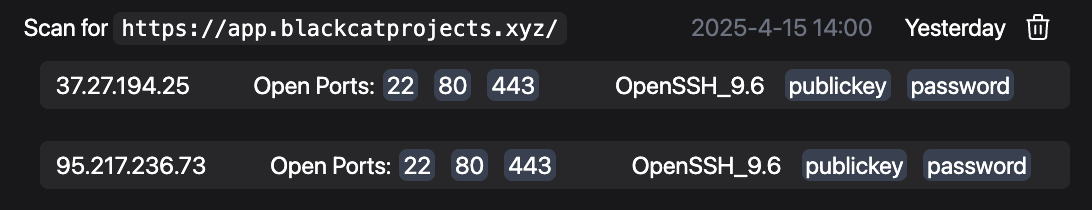
So both of these servers are not vulnerable. Note that it is possible for the Erlang SSH daemon to be running on a non-standard port, so if this server had say port 830 open, you would want to banner grab with netcat (nc) to confirm it is not running the Erlang SSH daemon.
Paraxial.io App Audit, which collects a list of all your application dependencies at runtime, can also be used to determine if you are affected. Go to the most recent App Audit for your site and search for “SSH”
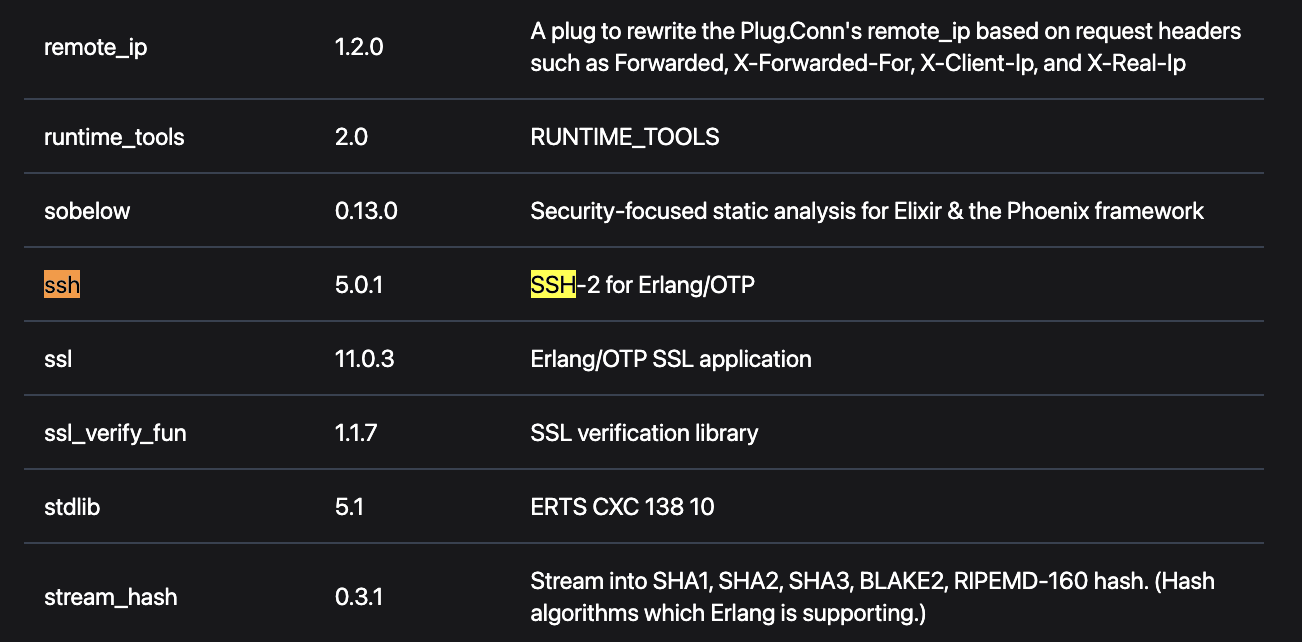
If there are 0 results for Ctrl+F “SSH”, then the application is not vulnerable. If the application is running a vulnerable version (as seen above), that does not necessarily mean it is exploitable by an attacker. The application must still be configured to expose the SSH service to the public internet in order for an attacker to connect to it and exploit CVE-2025-32433.
If you have questions or need security help, please feel free to send me an email - michael@paraxial.io
Thanks to Fabian Bäumer, Marcel Maehren, Marcus Brinkmann, and Jörg Schwenk from the Ruhr University Bochum for finding and responsibly disclosing this vulnerability to the Erlang/OTP project.
April 19, 2025 - This article was updated to include the new Nerves release and information about public PoC exploits.
April 21, 2025 - Updated information on which versions of Erlang’s SSH are vulnerable, Paraxial.io App Audit, and opening ports on Fly.io.
Paraxial.io stops data breaches by helping developers ship secure applications. Get a demo or start for free.