Free Rails Security Scan by Paraxial.io
Michael Lubas, 2025-01-23

Every Ruby on Rails application exposed to the public internet will be attacked by hackers scanning for SQL injection, remote code execution, and similar vulnerabilities that lead to total system compromise. This guide will cover the most relevant threats and how to take advantage of free Rails security scanning by Paraxial.io.
Threats
The most relevant threat to a Rails application is a server-side vulnerability, that is, a software flaw that an attacker can exploit by sending malicious requests to your application. Examples include:
- Command injection - Calling
eval(user_input)orsystem(user_input) - Deserialization - Calling
Marshal.loadon user input - SQL injection - Allowing an attacker to execute arbitrary SQL commands
- Exposed ports - Exposing Docker, Redis, MySQL, Postgres, etc to the public internet
All of these vulnerabilities are present in the OWASP Top 10 and can be prevented with Paraxial.io. You may be thinking that your project is not high profile enough to be targeted by attacks. The reality is any server exposed on the public internet will be scanned for security problems, and the best way to prevent an incident is to check your work and ensure these issues are not present.
How does Paraxial.io secure my Rails app?
This guide will cover:
- The Paraxial.io code (SAST) and dependency (SCA) scanning feature
- Runtime asset management
- License scanning
- Network level port scanning
All of these features are available on the free tier. To get started with Paraxial.io, register an account:
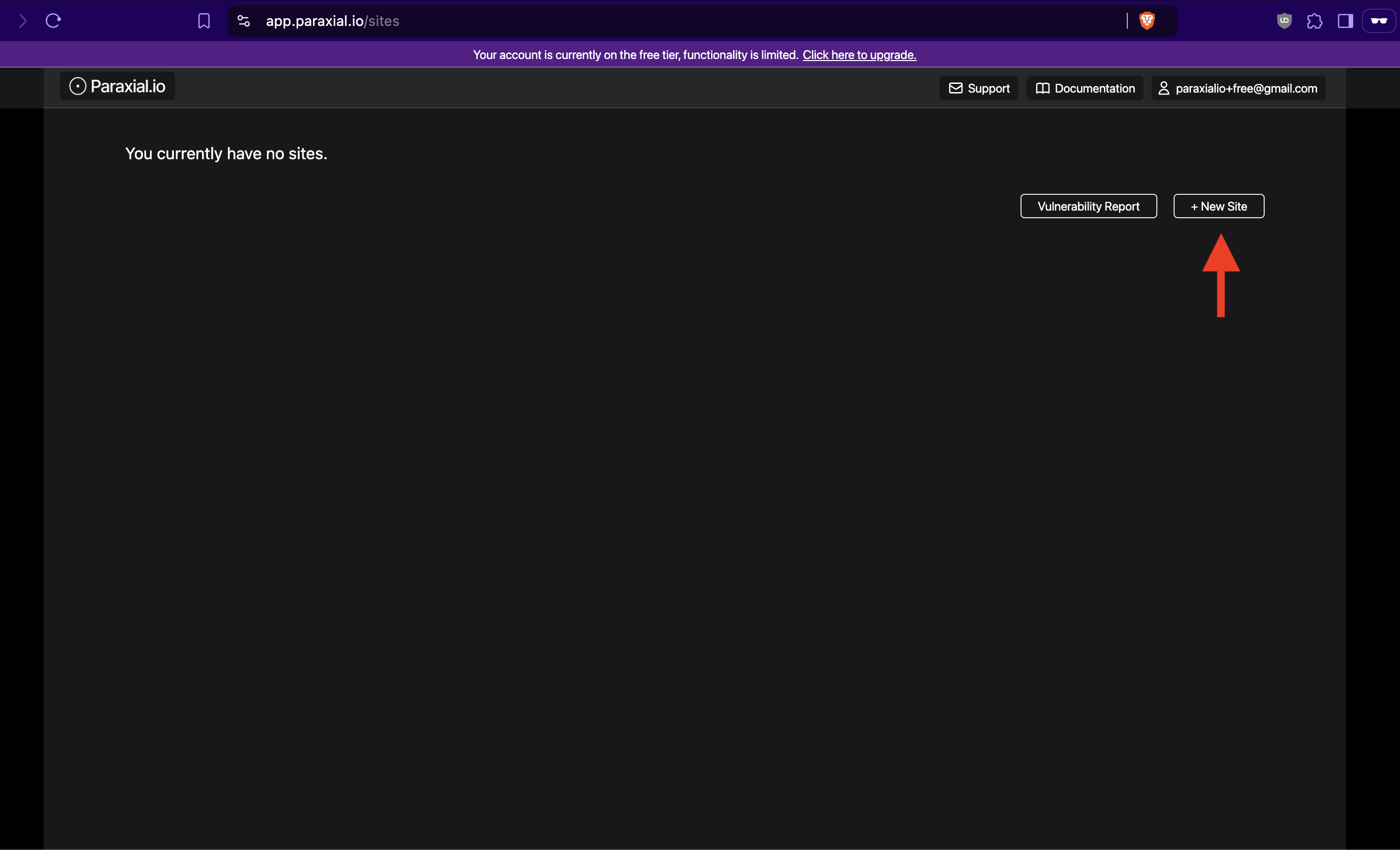
Then create your first site:
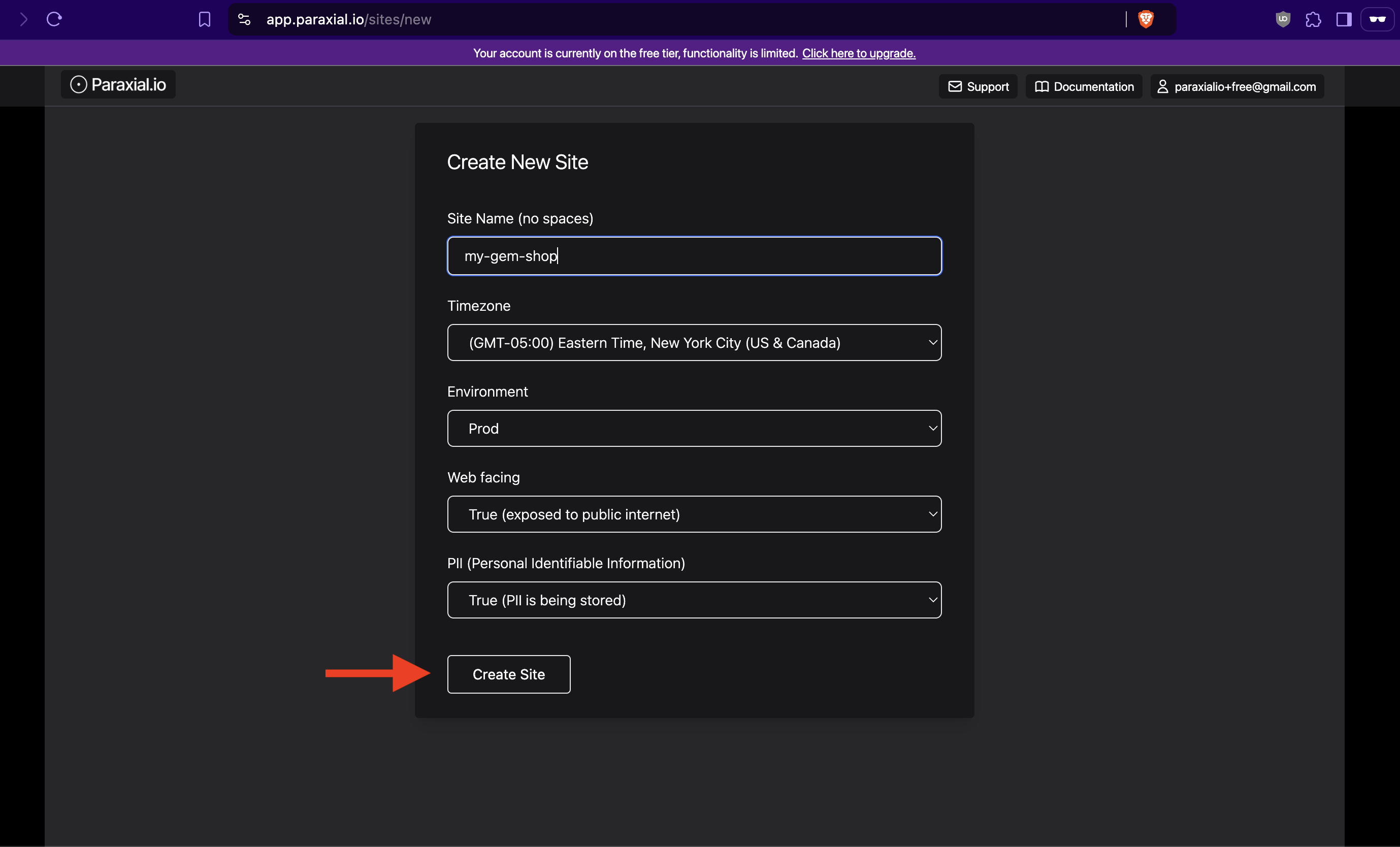
Enter the name of your Rails app:
Now that your Site is created, go to settings:
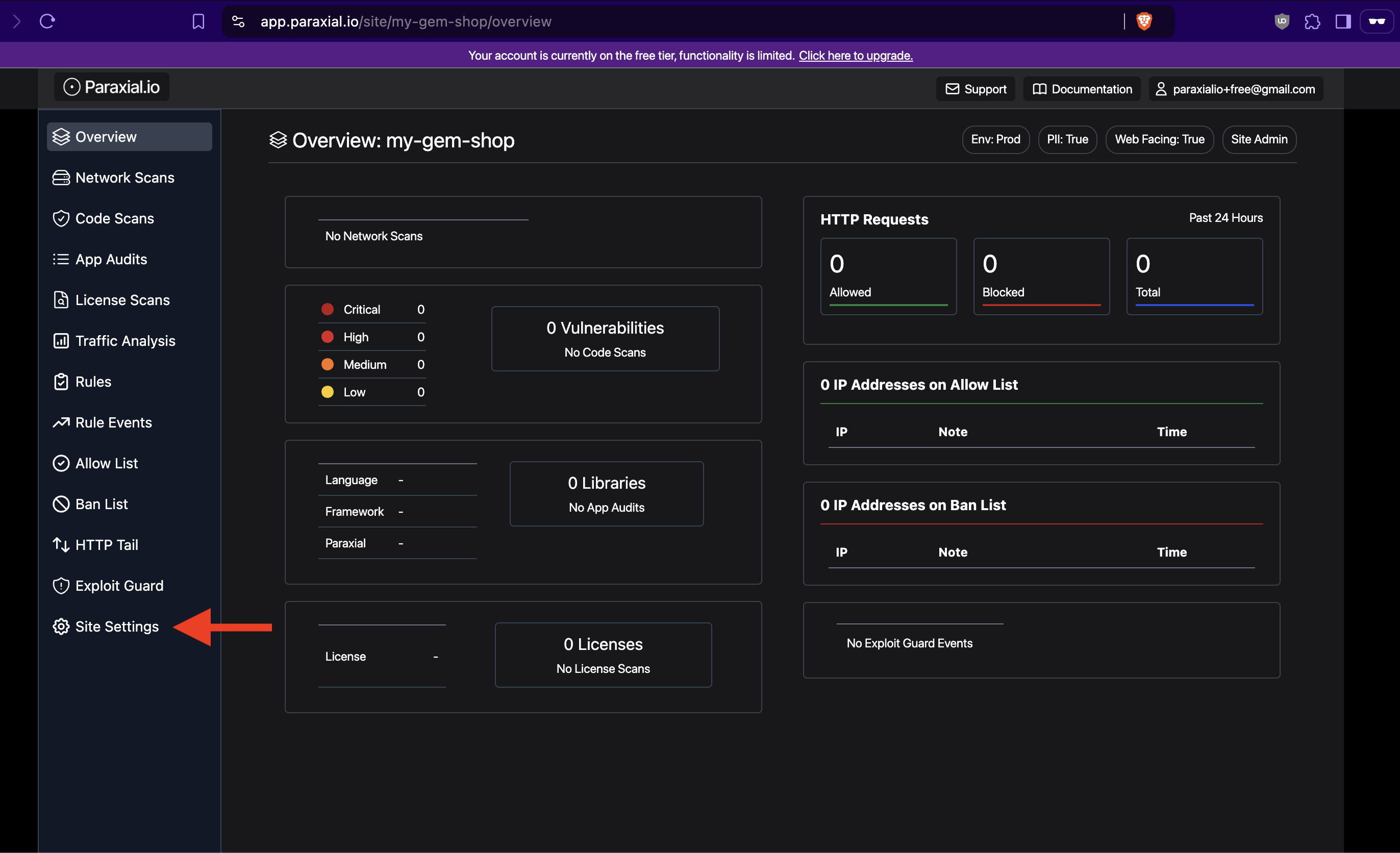
In settings, you will find your API key:

Now that you have your site API key, set your PARAXIAL_API_KEY env variable. To make it easier, you can update your .zshrc file (or system equivalent)
% vim ~/.zshrc
# Add the following line:
export PARAXIAL_API_KEY=YOUR_VALUEGem-Shop % source ~/.zshrc
Gem-Shop % echo $PARAXIAL_API_KEY
YOUR_VALUE_HEREInstall the Paraxial Gem in your project:
Gemfile
# Only install in development
group :development do
gem "paraxial", "~> 1.4.5"
endbundle
...
Gem-Shop % grep paraxial Gemfile.lock
paraxial (1.4.5)
paraxial (~> 1.4.5)Now you are ready to run your first scan:
Gem-Shop % paraxial scan
[Paraxial] v1.4.5 Scan starting...
[Paraxial] .paraxial-rubocop.yml does not exist. Creating file...
[Paraxial] .paraxial-rubocop.yml created.
[Paraxial] .paraxial.yml configuration file was not found. Using default configuration.
[Paraxial] Scan count: 11
(Gemfile.lock) actionpack: Possible Content Security Policy bypass in Action Dispatch - 8.0.0
- Title: actionpack: Possible Content Security Policy bypass in Action Dispatch
- Installed Version: 8.0.0
- Fixed Version: ~> 7.0.8.7, ~> 7.1.5.1, ~> 7.2.2.1, >= 8.0.0.1
...
(Rubocop) CSRF, action_dispatch.cookies_same_site_protection set to `nil` or `:none`.
- Path: config/initializers/content_security_policy.rb
- Line: 27
[Paraxial] Scan UUID ca836c2c-3401-4a99-94a3-92ebe9ffaf11
[Paraxial] Scan URL https://app.paraxial.io/site/my-gem-shop/scansYou can view the results of your scan in the web interface:
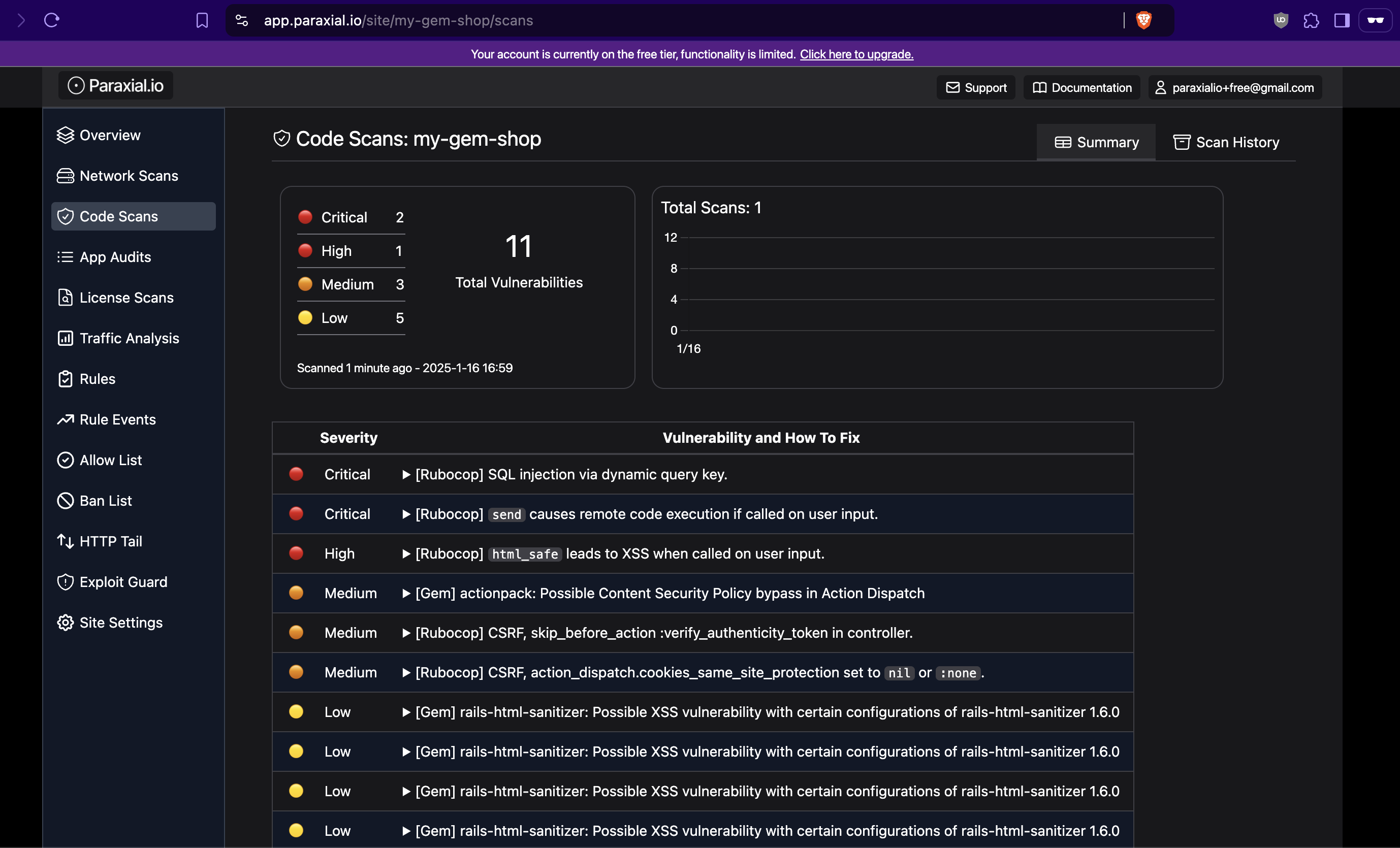
Next, start your application locally:
Gem-Shop % ./bin/dev
16:17:06 web.1 | started with pid 54975
16:17:06 css.1 | started with pid 54976
16:17:08 web.1 | => Booting Puma
16:17:08 web.1 | => Rails 8.0.0 application starting in development
...
16:17:09 css.1 | [Paraxial] v1.4.5 Agent starting...
16:17:09 css.1 | [Paraxial] API key detected, agent starting
16:17:09 css.1 | [Paraxial] Cloud IPs set
...
16:17:09 web.1 | Puma starting in single mode...
16:17:09 web.1 | * Puma version: 6.4.3 (ruby 3.3.4-p94) ("The Eagle of Durango")
...If you check the Overview page for your site, you should see data for App Audit and License Scan:
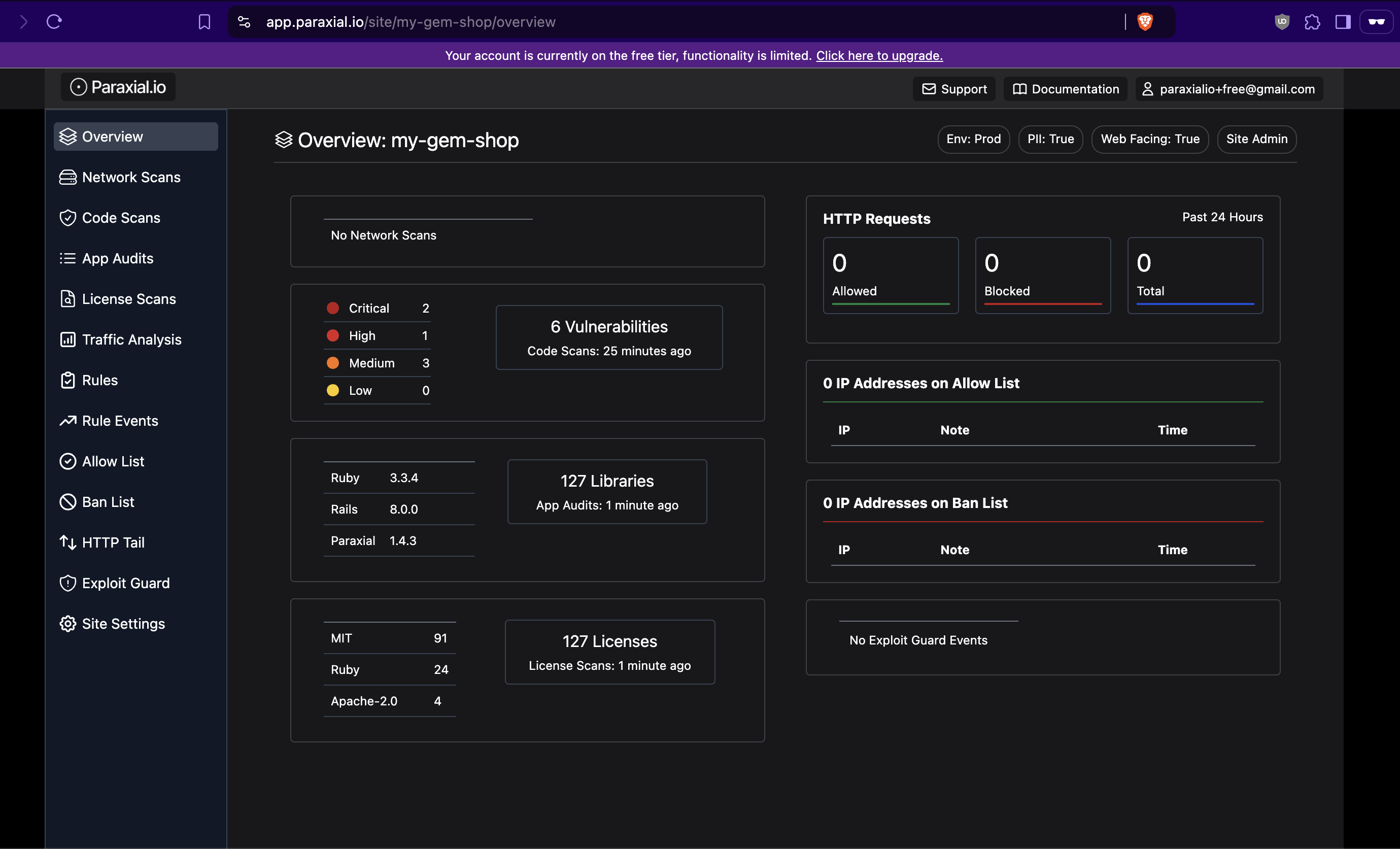
App Audit provides a list of every Gem dependency used by your application, collected at runtime. Why do this at runtime compared with the lockfile? The author of this post used to work on the security team of a company using Rails in production. A critical vulnerability was announced in a popular Gem one day, and if your company was running a specific version, say 2.7.11 or older, you were vulnerable. 2.7.12 and above were safe. Our first move was to search the lockfiles checked into GitHub to see what versions we were using, but there was no strong guarantee that these versions actually matched what was running in production. With App Audit, if you ever find yourself in a similar situation, you can be certain if you are safe from a major vulnerability.
License Scan is a feature which keeps track of the open source licenses your project is using across all dependencies. This is useful for businesses that need to be mindful of complying with the terms of all licenses currently in use.
The free tier of Paraxial.io includes the Network Scan feature, which is able to detect exposed ports on your server, for example MySQL on 3306. For more information about the risks of misconfiguring your server, see Security Best Practices for Deploying Rails 8 on Linux with Kamal.
Upgrading Your Account
Now that you have taken your first step towards secure Rails development, what’s next? Upgrading to a full Paraxial.io account includes the following benefits:
- Bot Defense (stops account takeover, credit card fraud, spam signups, etc)
- Ingest HTTP traffic to the Paraxial.io backend for analysis
- Greater than one site
- Add multiple users to your site
- Scan every new code change for security problems via CI/CD (no five scan/month limit)
- Access to the GitHub App with security guidance in the pull request
- Automated network scanning (daily, weekly)
- Priority support
Please use the free tier for non-commercial projects. To upgrade your account, contact support@paraxial.io.
Paraxial.io stops data breaches by helping developers ship secure applications. Get a demo or start for free.