Announcing Vulnerability Scanning and Management for Elixir
Paraxial.io, 2023-01-05

Paraxial.io now supports vulnerability scanning and management for Elixir applications. This is done via a mix task, which can be integrated into your CI/CD pipeline, that uploads the result of each scan to the Paraxial.io backend for tracking and reporting. This fulfills the compliance requirements for a number of security standards, and gives your team actionable metrics on the security of your project.
There are three popular security tools for ensuring the security of Phoenix applications:
- Sobelow, for static analysis of source code for vulnerabilities
- deps.audit, to scan a project's dependencies for vulnerabilities
- hex.audit, to scan for dependencies that have been marked as retired
It may seem straightforward to integrate these tools into your existing CI/CD pipeline, but consider the following questions:
- When was the last time the scan ran successfully?
- Do you have a record of when all these scans happened?
- Did the numbers of vulnerabilities increase or decrease compared to the previous scans?
- How do you view the findings of the most recent scan? Of a scan from 3 months ago?
With Paraxial.io’s Code Scan feature, you have all this information available in a convenient web interface. Each scan is started with a simple mix command:
mix paraxial.scanThe results of the scan are uploaded to the Paraxial.io backend, providing you with a record of all scans and findings for regulatory and compliance requirements.
Getting Started
Create a Paraxial.io account, after registration you will be taken to the “Sites” page.
We create a new site, felis-dev, for our project:
Then visit the code scans page:
In your Phoenix application, install the Paraxial agent via mix.exs
defp deps do
[
{:phoenix, "~> 1.6.15"},
{:phoenix_ecto, "~> 4.4"},
{:ecto_sql, "~> 3.6"},
...
{:paginator, "== 0.6.0"},
{:sobelow, "~> 0.11.1"},
{:paraxial, "~> 2.2.0"}
]
endmix deps.get
Update the configuration in config/dev.exs
config :paraxial,
paraxial_api_key: "API_KEY_REDACTED",
paraxial_url: "https://app.paraxial.io"With the Paraxial agent installed, you can now run a scan:
@ felis % mix paraxial.scan
13:07:24.329 [info] [Paraxial] API key found, scan results will be uploaded
Found retired packages
[Paraxial] Scan findings: %Paraxial.Scan{
api_key: "REDACTED",
findings: [
%Paraxial.Finding{
content: %{
"confidence" => "high_confidence",
"file" => "lib/felis_web/controllers/page_controller.ex",
"line" => 12,
"type" => "DOS.StringToAtom: Unsafe `String.to_atom`",
"variable" => "color"
},
source: "sobelow"
},
%Paraxial.Finding{
content: %{
"confidence" => "high_confidence",
"file" => "config/prod.exs",
"line" => 0,
"type" => "Config.HTTPS: HTTPS Not Enabled"
},
source: "sobelow"
},
%Paraxial.Finding{
content: %{
"confidence" => "high_confidence",
"file" => "lib/felis_web/router.ex",
"line" => 10,
"pipeline" => "browser",
"type" => "Config.CSP: Missing Content-Security-Policy"
},
source: "sobelow"
},
%Paraxial.Finding{
content: %{
"First patched versions" => " 1.0.0",
"Lockfile" => " /Users/dt/paraxial_repos/felis/mix.lock",
"Name" => " paginator",
"Severity" => " critical",
"Title" => " Remote Code Execution in paginator",
"URL" => " https://github.com/advisories/GHSA-w98m-2xqg-9cvj",
"Version" => " 0.6.0",
"Vulnerable versions" => " < 1.0.0"
},
source: "deps.audit"
},
%Paraxial.Finding{
content: %{
"dependency" => "mojito",
"reason" => "(deprecated) Mojito is now deprecated, use Finch instead: https://github.com/sneako/finch",
"version" => "0.7.12"
},
source: "hex.audit"
},
%Paraxial.Finding{
content: %{
"dependency" => "paginator",
"reason" => "(security) Remote Code Execution Vulnerability",
"version" => "0.6.0"
},
source: "hex.audit"
}
],
timestamp: ~U[2023-01-03 18:07:25.825954Z]
}
13:07:26.498 [info] [Paraxial] Scan upload successAnd view the results:
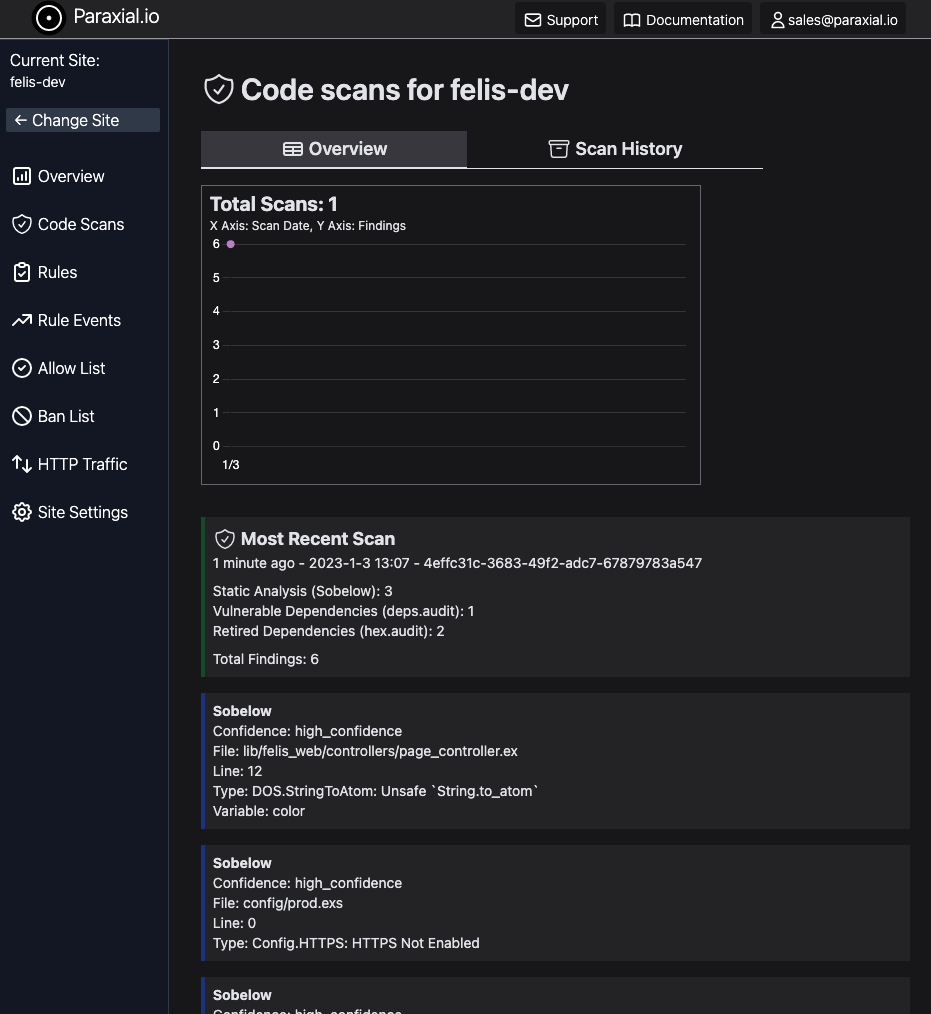
To eliminate the findings due to deprecated and vulnerable packages, we remove them for this example. In your real application you could also upgrade them.
defp deps do
[
{:phoenix, "~> 1.6.15"},
...
{:jason, "~> 1.2"},
{:plug_cowboy, "~> 2.5"},
{:httpoison, "~> 1.8"},
#{:mojito, "~> 0.7.12"},
#{:paginator, "== 0.6.0"},
{:sobelow, "~> 0.11.1"},
{:paraxial, "~> 2.2.0"}
]
endmix deps.unlock --all
mix deps.get
mix paraxial.scan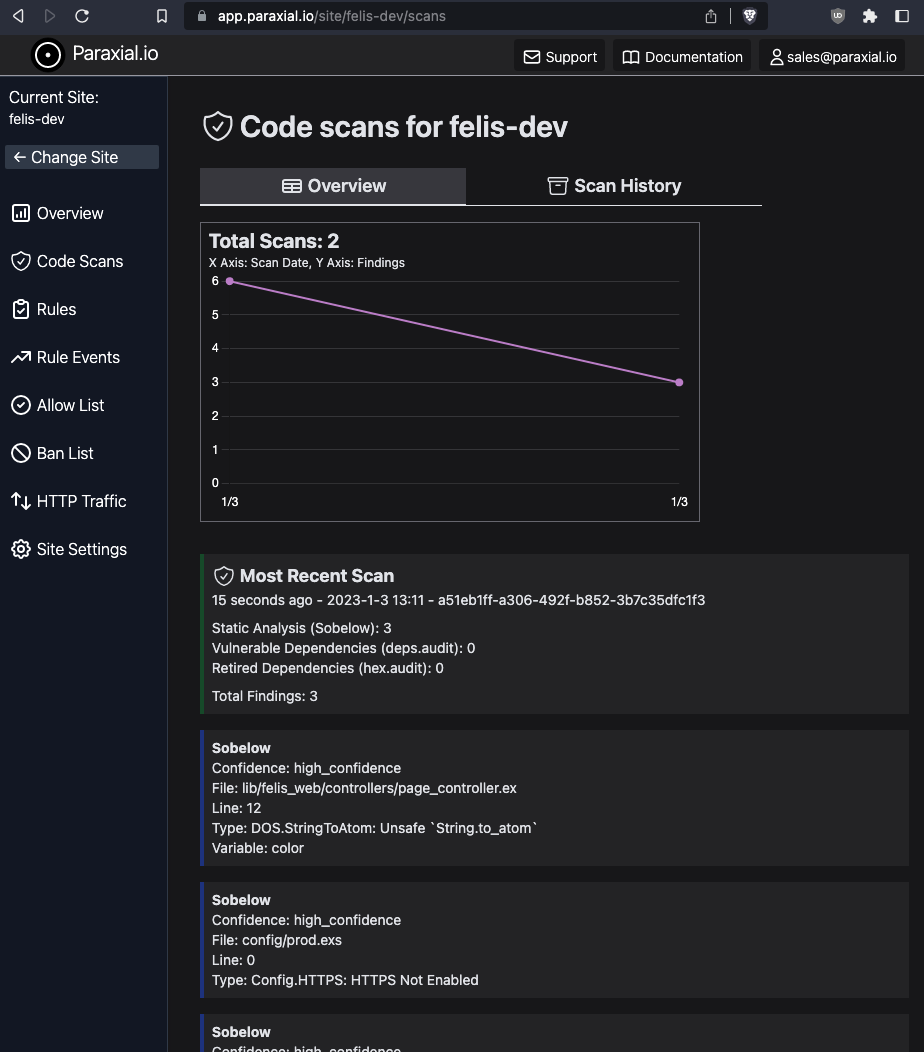
The remaining vulnerabilities are from Sobelow, which provides a flag to mark all current findings as skippable, if all the current findings are false positives:
@ felis % mix sobelow --mark-skip-allCheck for the creation of a .sobelow-skips file:
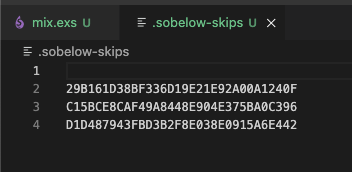
Then run mix paraxial.scan:
@ felis % mix paraxial.scan
13:13:21.052 [info] [Paraxial] API key found, scan results will be uploaded
[Paraxial] Scan findings: %Paraxial.Scan{
api_key: "REDACTED",
findings: [],
timestamp: ~U[2023-01-03 18:13:22.353607Z]
}
13:13:22.993 [info] [Paraxial] Scan upload success
@ felis % 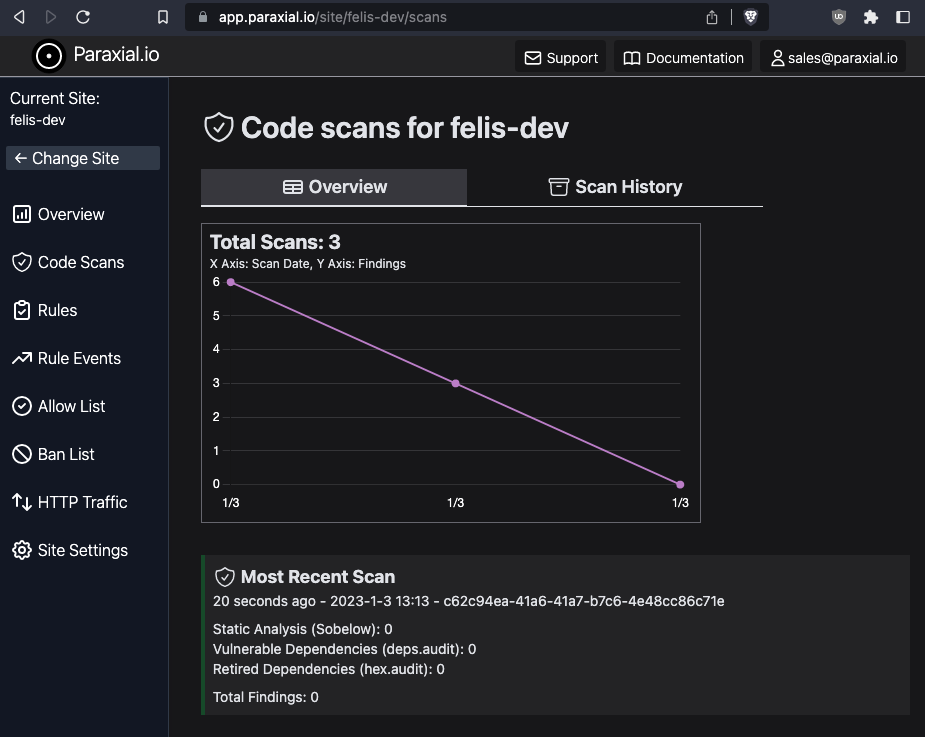
The Sobelow findings have been successfully excluded from future scans. You can also view a full history of every scan.
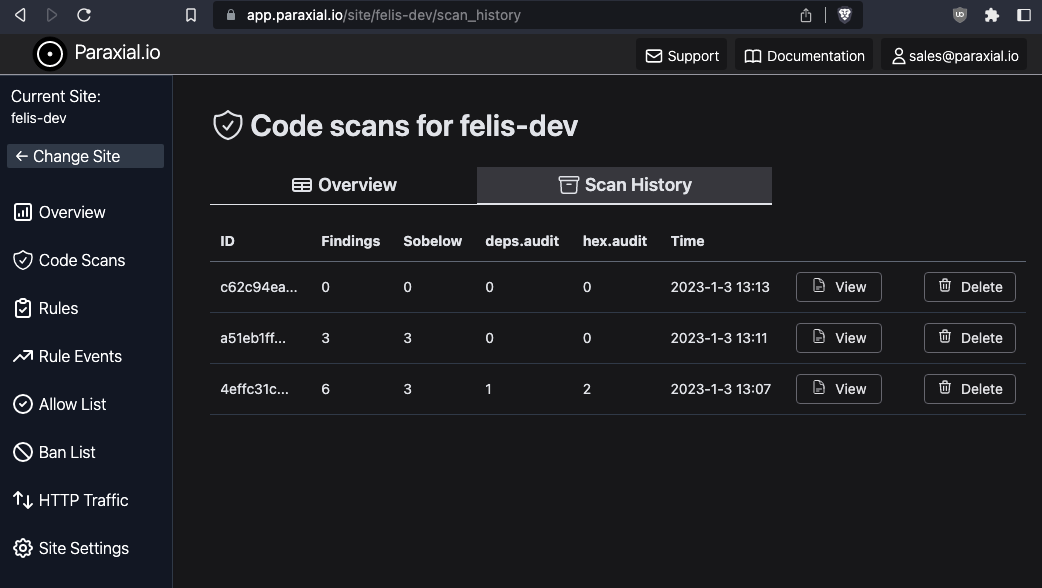
Paraxial.io stops data breaches by helping developers ship secure applications. Get a demo or start for free.