Ban Bots Scanning for Vulnerable WordPress with Paraxial.io
Michael Lubas, 2024-11-12
All web applications on the public internet will be targeted by automated malicious scanners. A common example is WordPress, due to how many sites use it, and the high number of exploitable bugs. If you have a Ruby or Elixir app, a malicious bot scanning for WordPress vulnerabilities does not pose a real threat, because the exploit being used will not work. There are several good reasons to still ban the offending IP:
- The IP is malicious, and may decide to start scanning with compatible payloads.
- The extra traffic leads to an increase in your cloud hosting bill and incorrect metrics.
- Banning the IP deters future attacks, an automated system may move on to different targets.
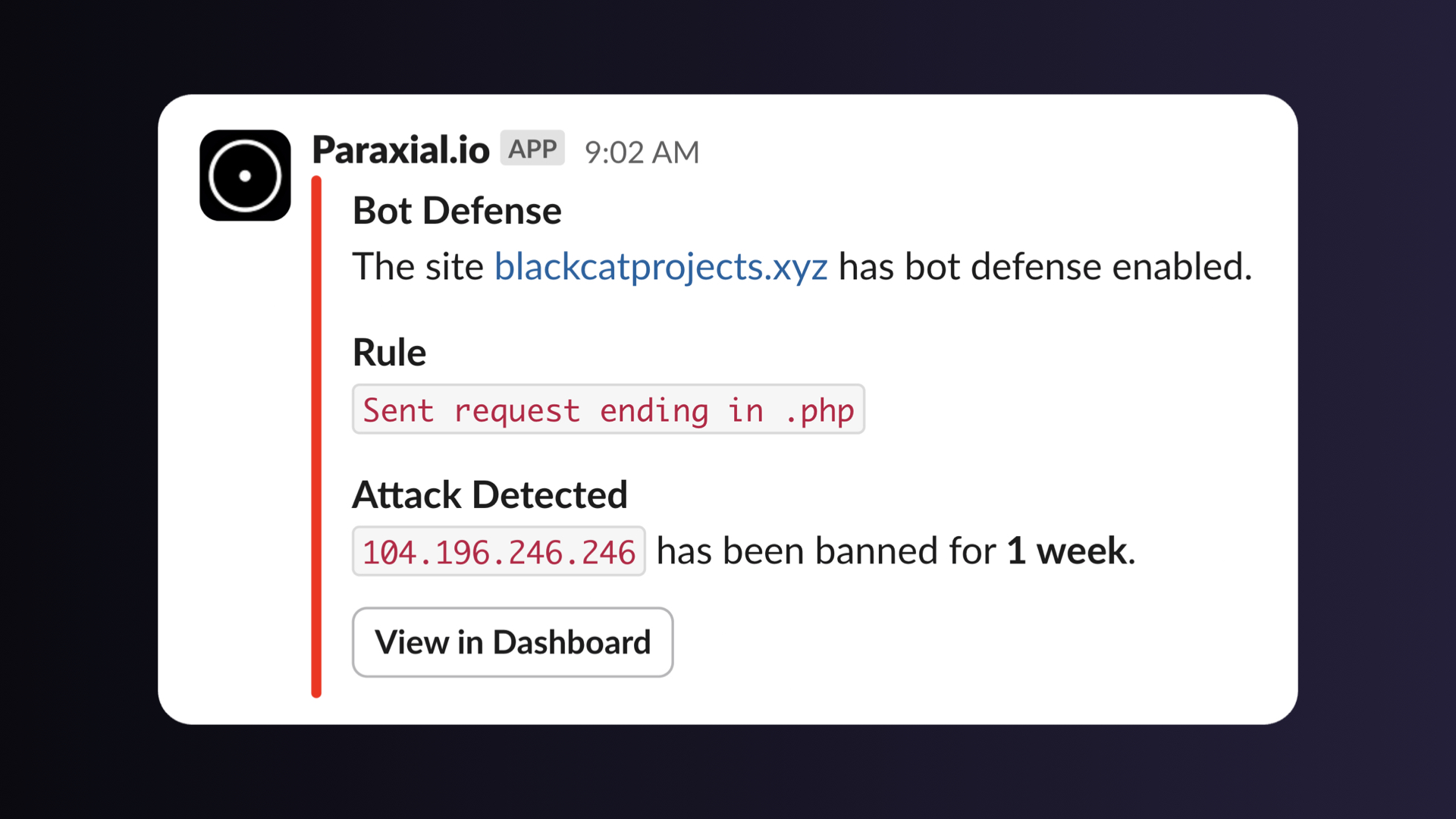
Paraxial.io now supports banning clients that send a request ending in .php (a classic sign of this attack) out of the box:
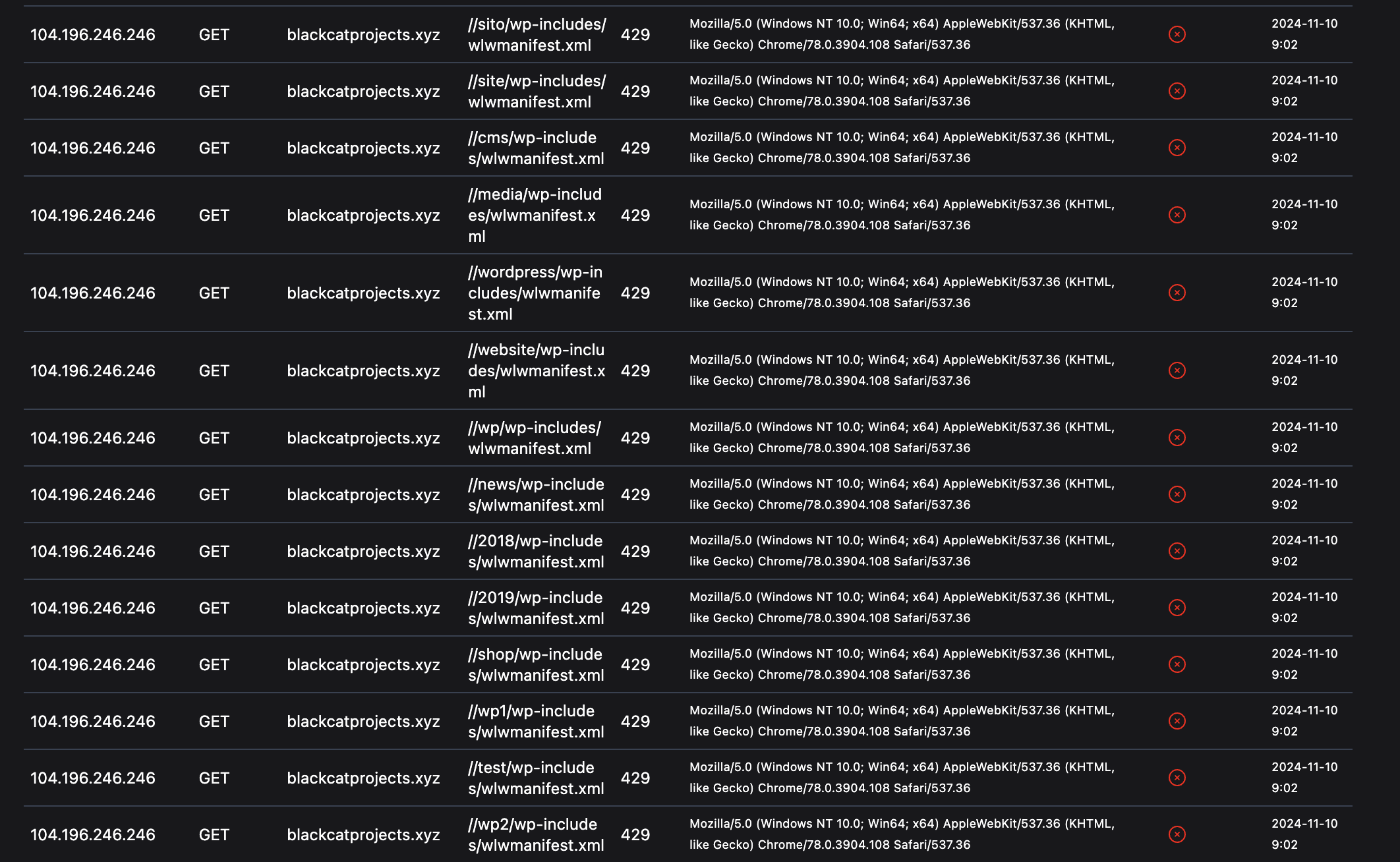
Below is a real attacker who was banned after sending a GET request to /xmlrpc.php
The documentation above also shows how to implement your own banning logic. Have you seen a targeted attack to a specific endpoint or from certain user agents? You can write custom middleware to ban on the exact conditions needed. With the Paraxial.io Slack App, you can even receive a notification on new ban events.
This feature is available on the Paraxial.io Free Tier, including Slack notifications. Sending HTTP requests to the backend (as seen in the previous screenshot) does require a paid plan.
Paraxial.io stops data breaches by helping developers ship secure applications. Get a demo or start for free.