Secure Asset Management in Elixir with Paraxial.io
Michael Lubas, 2024-01-24
In March 2017 an important security patch for Apache Struts was released, due to a vulnerability with public examples showing how to break into a running server. Apache Struts is to Java what Rails is to Ruby, and Phoenix is to Elixir. Equifax, a major credit bureau, did not have an inventory of every server running Apache Struts, and in May 2017 the highest profile breach ever began with a hacked web server, ending with a $425 million settlement.
When news of a critical security problem becomes public, suddenly the number one priority of an organization’s security team is finding the web facing servers running the vulnerable code, then patching them before an attacker gets in. Proper defense requires a comprehensive inventory of your apps. This is an important milestone, I ranked it number one in the publication Elixir Security Roadmap: A CTO Level Guide because it is the foundation of an effective security program. For many organizations this work is not a high priority until it is too late.
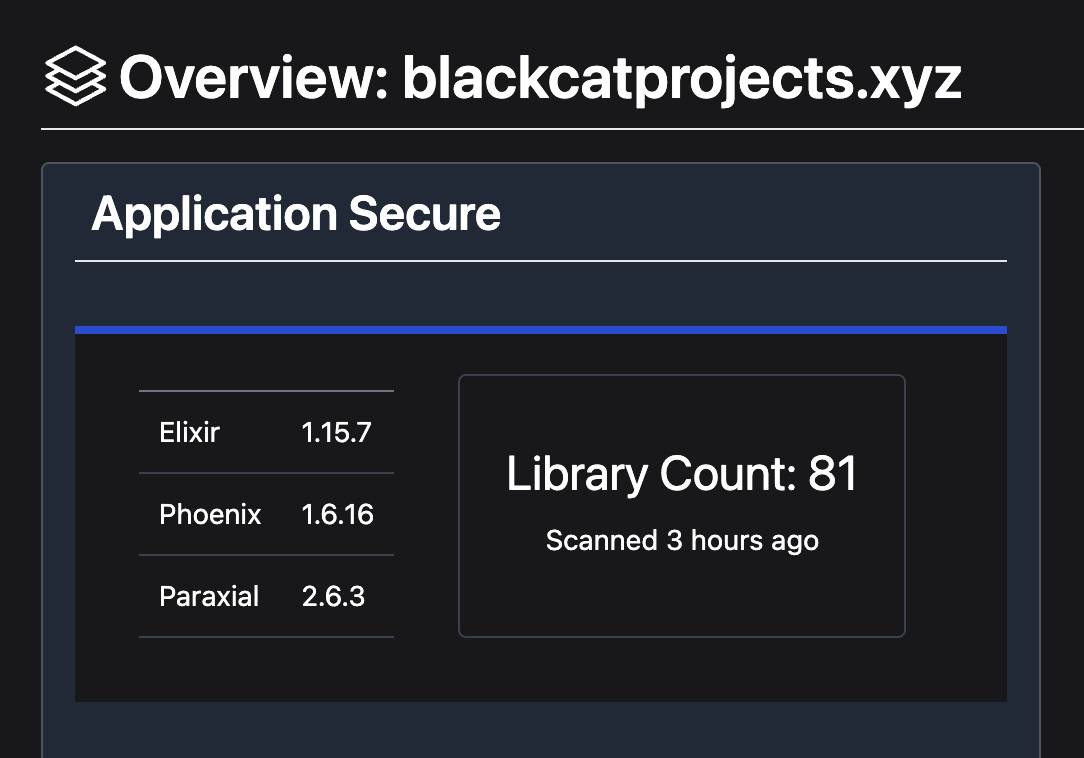
Paraxial.io is by far the best way to get an accurate inventory of Elixir and Phoenix apps, because it automates the entire process. The Elixir agent is installed as a normal dependency in your mix.exs file. Paraxial.io gets an inventory of all dependencies at runtime. The benefit of doing this, instead of lockfile inspection, is that the lockfile checked into Git does not always match production. Getting this data at runtime means it is the most accurate picture of your infrastructure.
Not all Elixir apps in a company are of equal security importance. Which is a higher priority: the production web facing product that stores sensitive personally identifiable information (PII) about customers, or an internal-only tool that does not have any PII? One code base may be deployed in multiple environments, for example production, development, and testing. The Paraxial.io interface is able to summarize all this information.
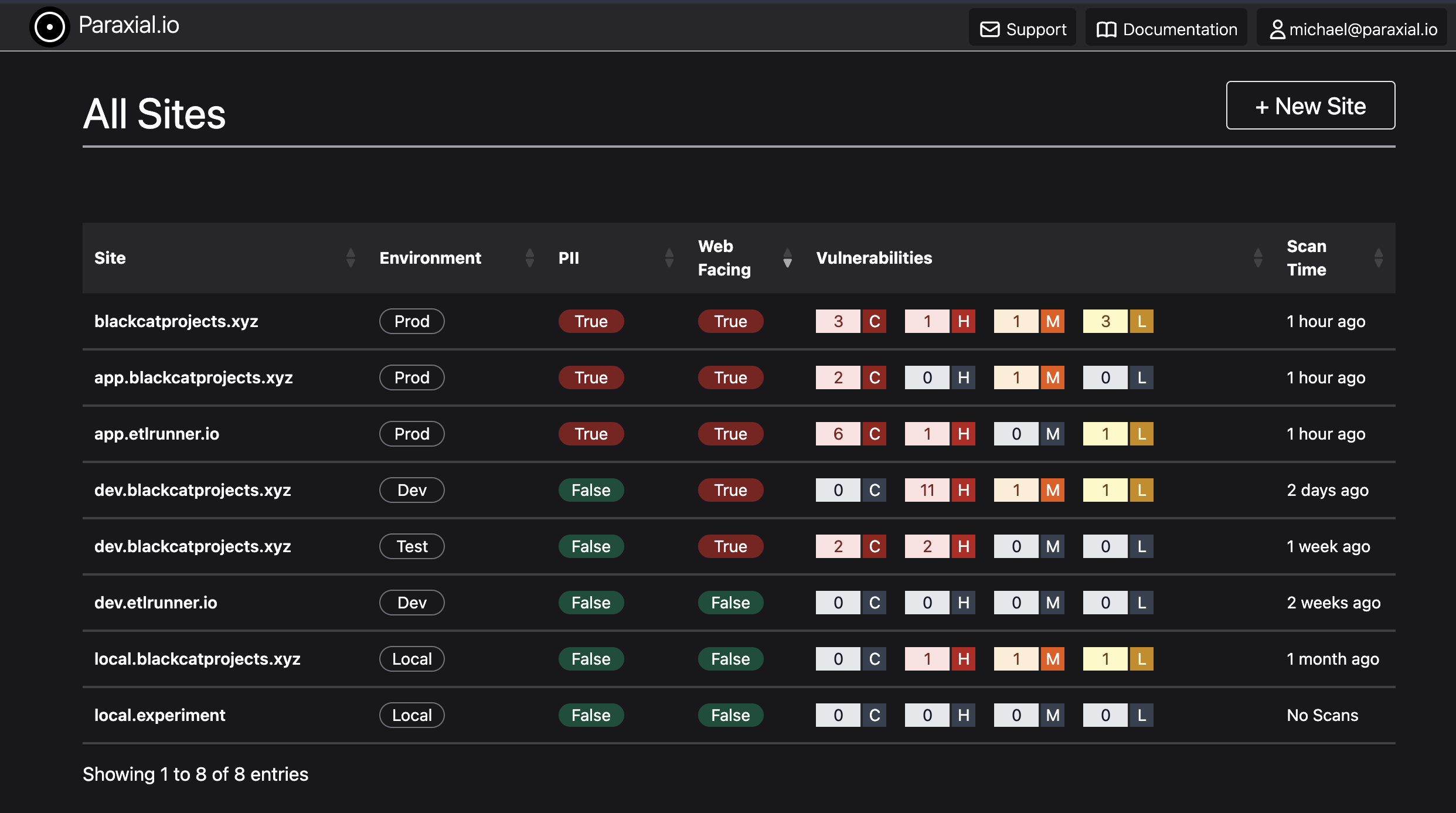
The vulnerabilities column displays code scan findings by severity: critical, high, medium, or low. These are the result of a Paraxial.io code scan, which checks source code and dependencies for security issues. The scans are usually performed as part of a CI/CD pipeline, and then feedback is shown to developers through the GitHub App. Having this dashboard available is important, yet checking the security software is not always part of people’s daily workflow. Paraxial.io also sends a weekly email summary with this information.
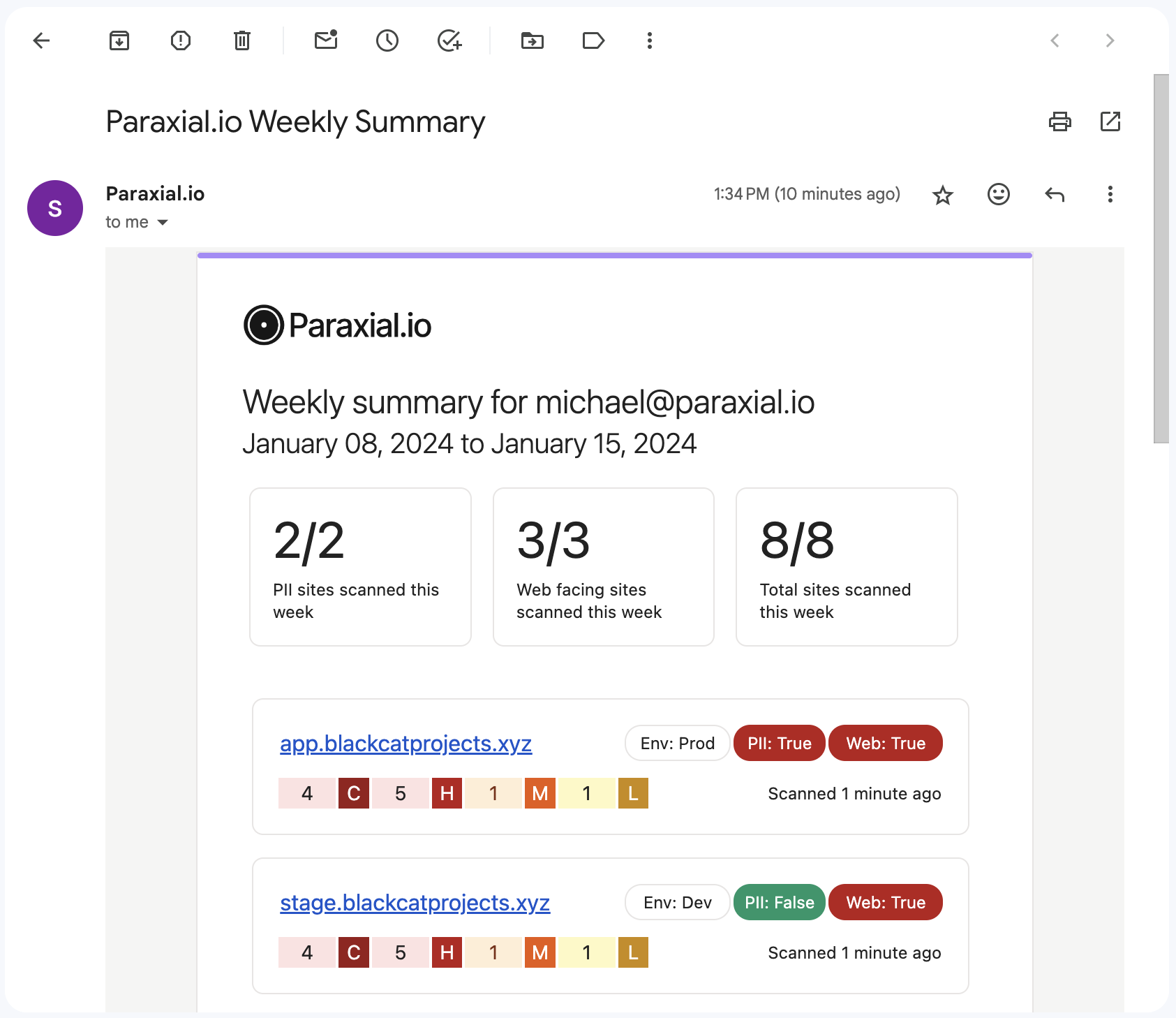
Sites that are vulnerable to attack are highlighted here. If you are currently a Paraxial.io customer, all these features are live now. If you would like to start using Paraxial.io, please reach out today.
Paraxial.io stops data breaches by helping developers ship secure applications. Get a demo or start for free.